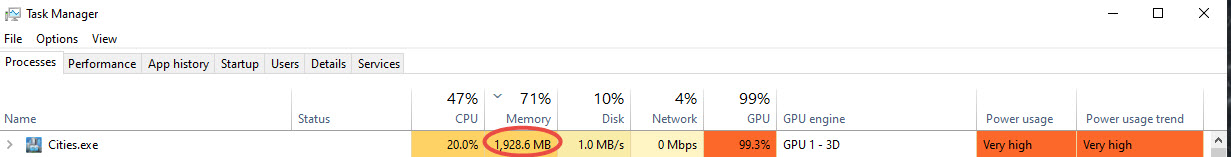
The Cities: Skylines game keeps objects in memory even if the object is not used. Even a 16GB system can crash frequently if the memory usage is not managed.
“Oops! The game crashed
The memory usage is high, even when the map is not too complex.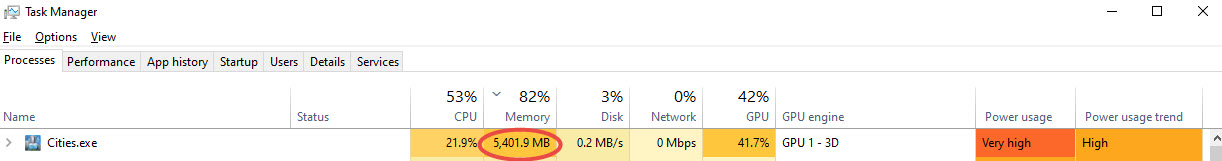
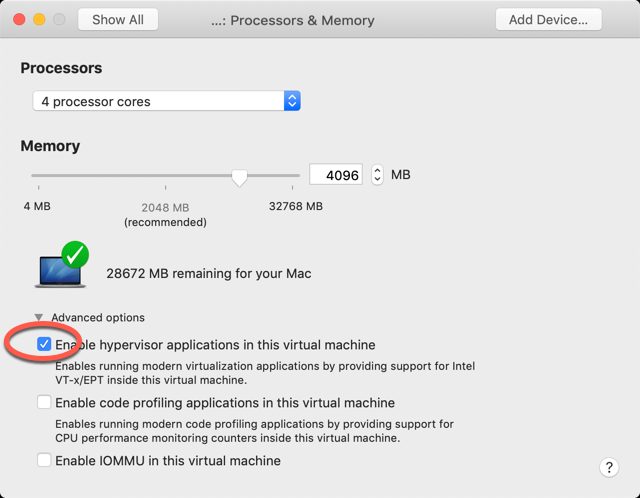
Enable enough Virtual Memory
Make sure Windows has enough Virtual Memory configured. I have set up 4096 MB minimum and maximum Virtual Memory for my 16 GB Toshiba laptop.
Install the Loading Screen mod
This page explains the issue and how to solve the problem: https://steamcommunity.com/app/255710/discussions/0/1488866180604646672/
This is the summary of the steps you can take to stabilize the game on your computer
- Get the Loading Screen Mod at https://steamcommunity.com/sharedfiles/filedetails/?id=667342976
- Read the guide to understand the skipping the prefabs at https://steamcommunity.com/workshop/filedetails/discussion/667342976/1741105805762370419/
- The prefab names are listed at https://thale5.github.io/Prefabs/
- Download the sample “skip.txt” file from https://thale5.github.io/Prefabs/ and save it at
C:\Users\YOUR_USER_NAME\AppData\Local\Colossal Order\Cities_Skylines\SkippedPrefabs\skip.txt - Start the Cities: Skylines game and select CONTENT MANAGER

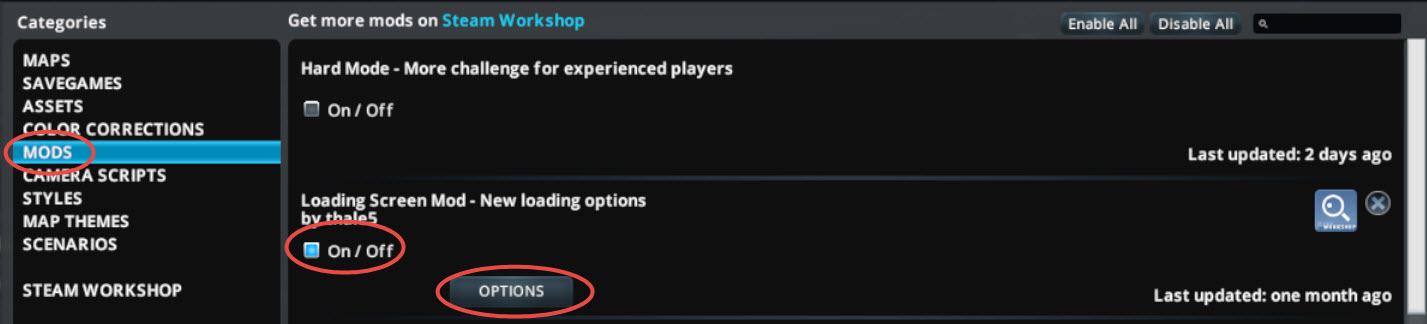
- On the left side select MODS
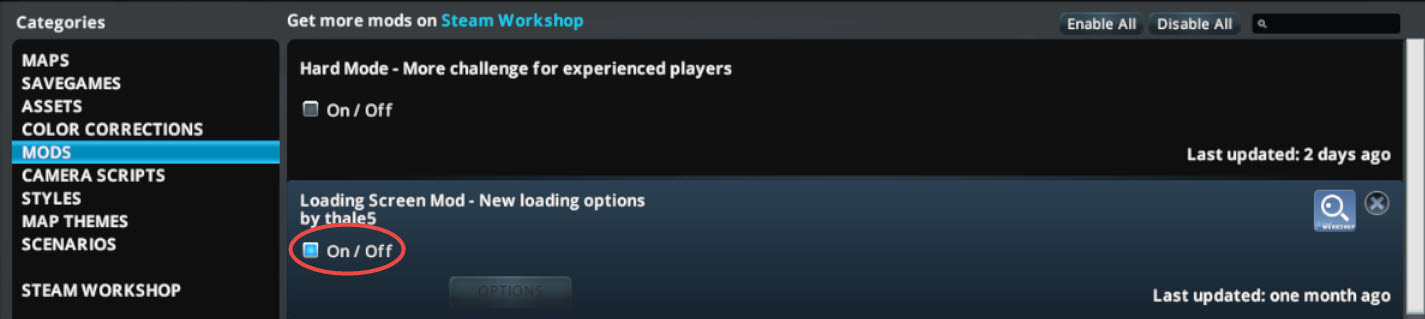
- Enable the mod. We will be able to set the options when the mod already ran once.
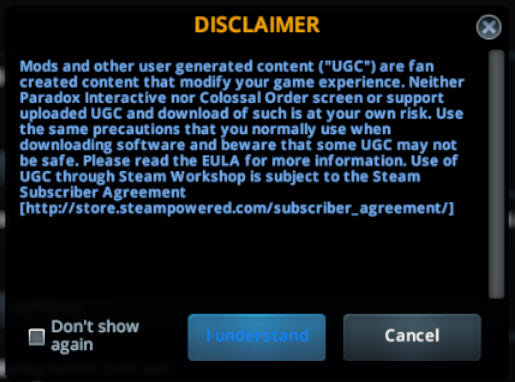
- Accept the disclaimer
- Close the MODS page
- Start the game to be able to set the options later

- Quit the game
- Exit to the Main Menu
- Open the MODS page

- Click the OPTIONS button
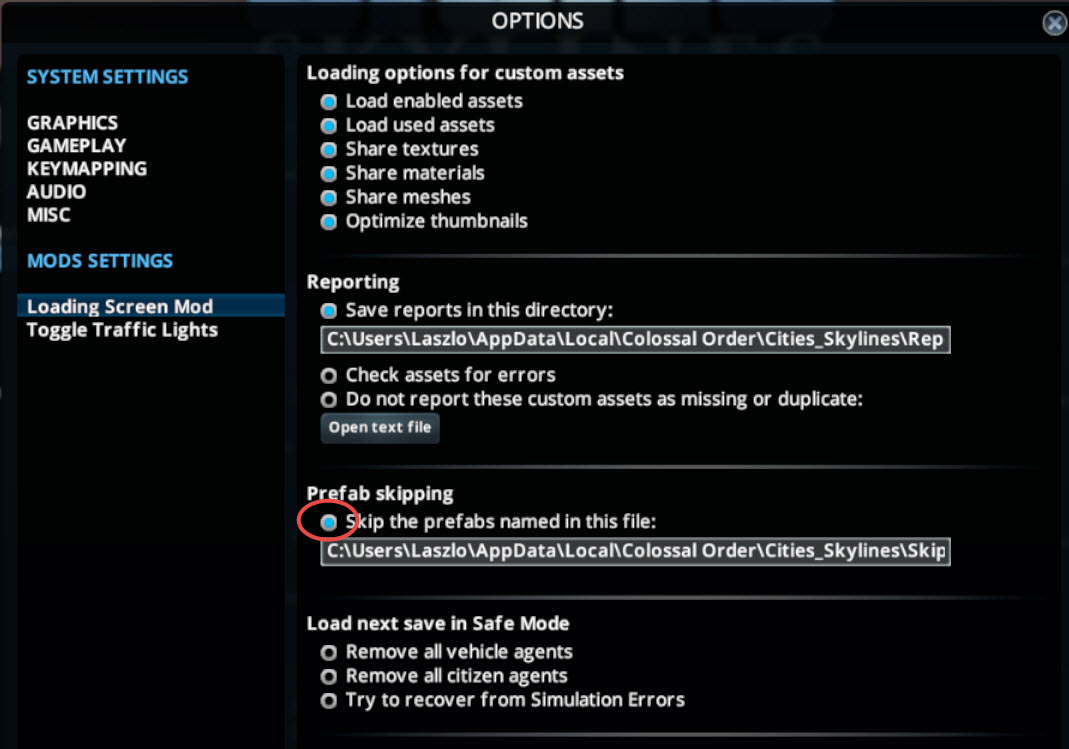
- Select the Skip the prefabs named in this file option
- When the game starts the Loading Screen mod will display the memory usage
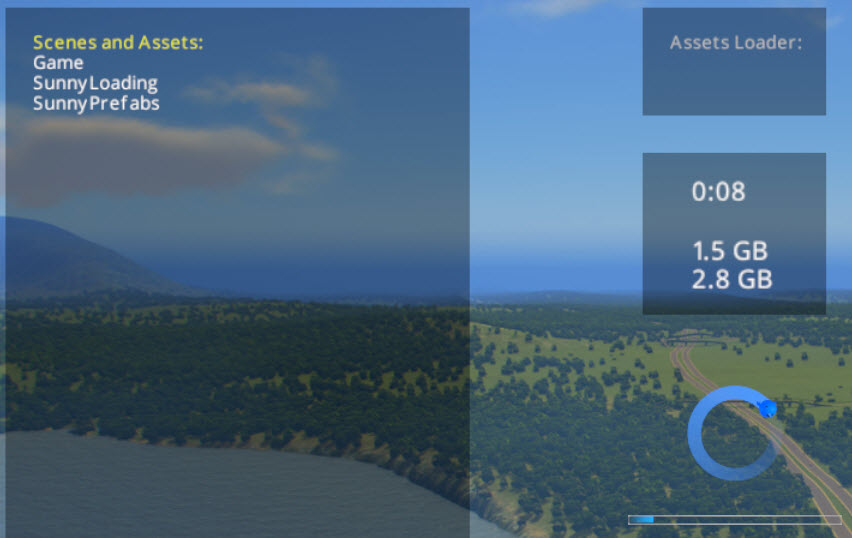
- After a few minutes, the memory usage will go down to 25% of the prior value or less.