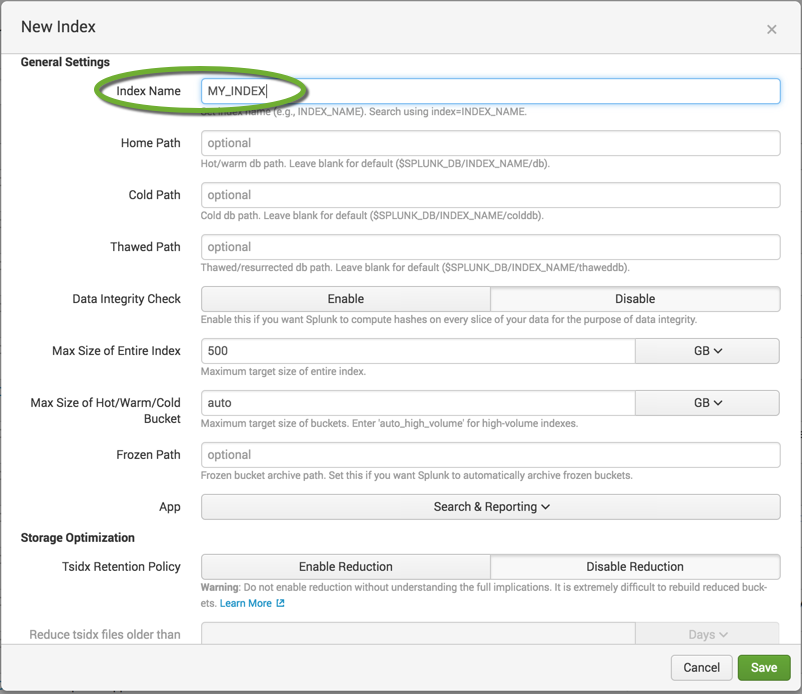
Splunk stores the events in separate databases based on index names. It is faster to search for events if the event types are separated into multiple indexes.
To create an index for the event type you want to send to Splunk
- In the Settings menu select Indexes
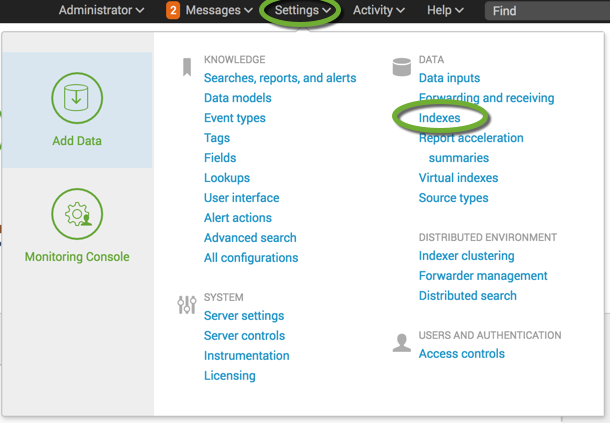
- Click the New Index button
- Enter the name of the index. You can leave the default settings, and click the Save button.